Headphone maker Sennheiser has patched its software after the company admitted a serious vulnerability that made it easy for hackers to impersonate any website — even encrypted pages.
The software, which helps Mac and Windows users to connects their headphones to other devices, also installed a self-signed root certificates with an easily obtainable private key. Because the key was stored in the operating system’s certificate store and the same key was used on every installation, it was easy for anyone to create their own certificate on a website to look like the original website — even when it isn’t.
That makes it easy for phishing, credential stealing, or spreading malware and disinformation when it looks like it’s coming from the original, legitimate source.
“The victim would have to inspect the HTTPS server certificate respectively code signing certificate in a detail level that shows the root certificate to which the certificate in question is linked,” said the report by Secorvo’s Hans-Joachim Knobloch and André Domnick, published this week.
But most people never do — they see a green padlock and assume the best.
To prove their point, the researchers created a wildcard certificate that spoofed Google’s homepage, making it look almost impossible to distinguish rom the real site.
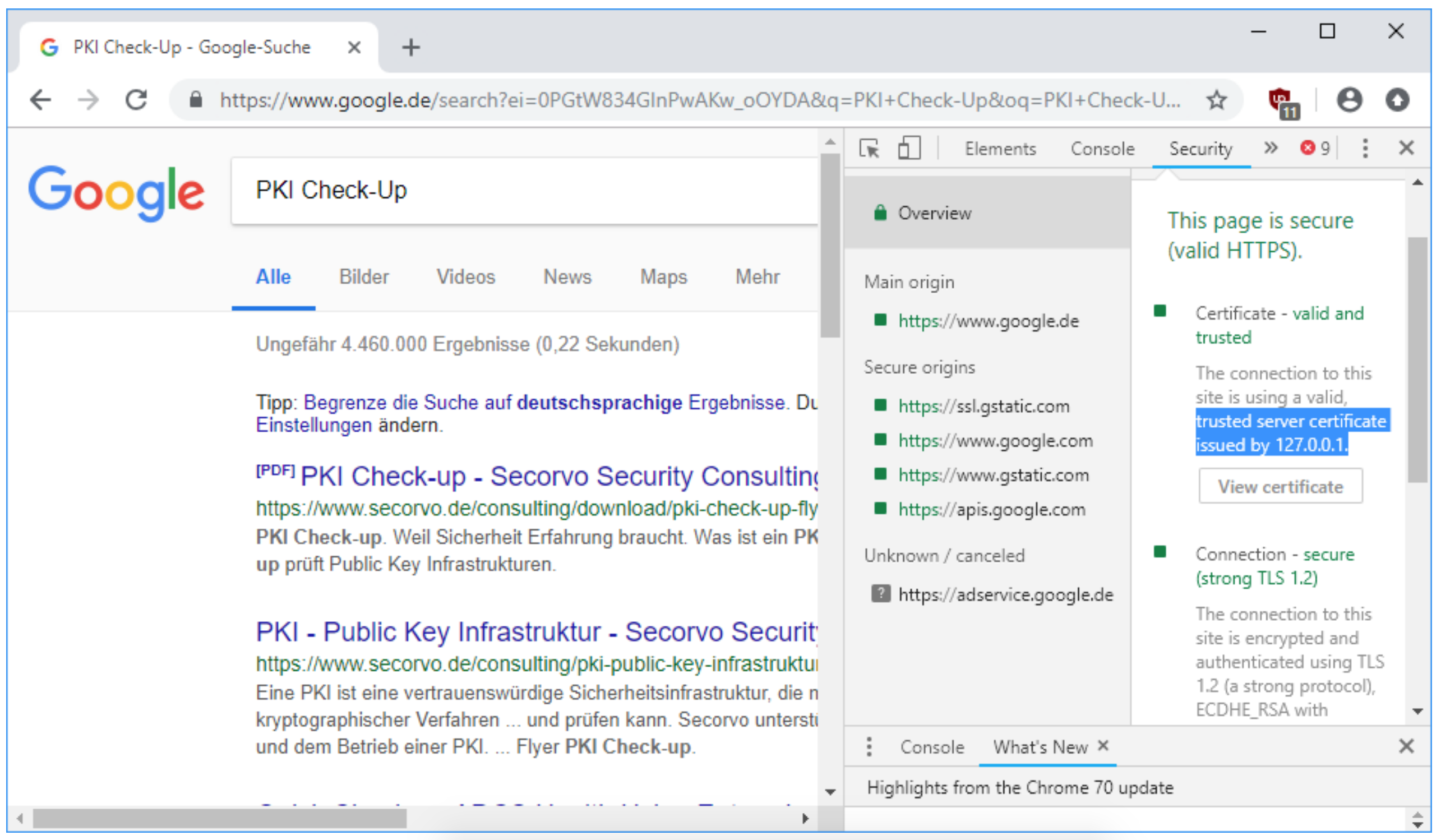
An example of Chrome accepting the attacker’s certificate. (Image: Secorvo)
Make no mistake: this was a monumental security flaw that put every Sennheiser software user at risk. But what made matters worse is that removing the software wouldn’t remove the certificate — leaving them still vulnerable to spoofing and impersonation attacks.
“Since the certificate is not removed from the trusted root certificate store during update or removal of the software, every system on which HeadSetup 7.3 was installed at any time in the past – and every user on such a system – remains vulnerable,” said the report.
Sennheiser later issued a software update that remediated the vulnerability by updating the root store with a new certificate that omitted the private key.
Microsoft also released its own advisory this week, warning users of the inadvertently disclosed certificate and private key. The software giant updated its own certificate trust list to protect Windows users from certificate spoofing by throwing an error.
Cast your mind back to 2015 and you might remember a similar security scandal: the Superfish adware, which shipped preinstalled in Lenovo PCs.
Like Sennheiser, Superfish contained a certificate that effectively allowed the company to man-in-the-middle the user’s connection and inject ads — even when the connection is encrypted and believed to be “secure.” The key was made public, allowing anyone to take advantage of the weakness while on the same network.
Lenovo was later fined $3.5 million for the security lapse.
from TechCrunch https://ift.tt/2RoE0P0
via IFTTT
Comments
Post a Comment