Google today announced a number of upcoming changes to how Chrome will handle extensions that request a lot of permissions, as well as new requirements for developers who want to publish their extensions in the Chrome Web Store.
It’s no secret that no matter which browser you use, extensions are one of the main vectors that malicious developers use to gain access to your data. Over the years, Google has improved its ability to automatically detect malicious extensions before they ever make it into the store. The company also made quite a few changes to the browser itself to ensure that extensions can wreak havoc once they have been installed. Now, it’s taking this a bit further.
Starting with Chrome 70, users can restrict host access to their own custom list of sites. That’s important because, by default, most extensions can see and manipulate any website you go to. Whitelists are hard to maintain, though, so users can also opt to only provide an extension with access to the current page after a click.
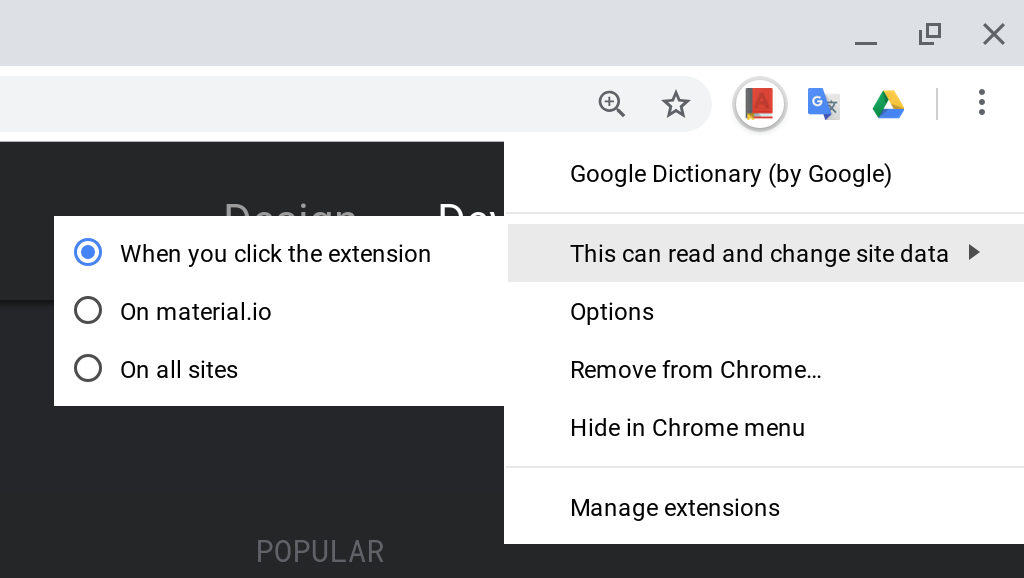
“While host permissions have enabled thousands of powerful and creative extension use cases, they have also led to a broad range of misuse — both malicious and unintentional — because they allow extensions to automatically read and change data on websites,” Google explains in today’s announcement.
Any extensions that request what Google calls “powerful permissions” will now also be subject to a more extensive review process. In addition, Google will also take a closer look at extensions that use remotely hosted code (since that code could be changed at any time, after all).
As far as permissions go, Google also notes that in 2019, it’ll introduce new mechanisms and more narrowly scoped APIs that will reduce the need for broader permissions and that will give users more control over the access that they grant to their extensions. Starting in 2019, Google will also require two-factor authentication for access to Chrome Web Store developer accounts to make sure that a malicious actor can’t take over a developer’s account and publish a hacked extension.
While that change is still a few months out, starting today, developers are no longer allowed to publish extensions with obfuscated code. By default, obfuscated code isn’t a bad thing. Developers often use this method of scrambling their JavaScript source code to hide their code, which would otherwise be in clear text and easy to steal. That also makes it very hard to figure out what exactly the code does, and 70 percent of malicious extensions and those that try to circumvent Google’s policies use obfuscated code. Google will remove all existing extensions with obfuscated code in 90 days.
It’s worth noting that developers will still be allowed to minify their code to remove whitespace, comments and newlines, for example.
from TechCrunch https://ift.tt/2NeZsCR
via IFTTT

No comments:
Post a Comment