Phishing actors are following a new trend of targeting non-executive employees but who still have access to valuable areas within an organization.
As reported by Avanan researchers, half of all phishing emails they analyzed in recent months impersonated non-executives, and 77% of them targeted employees on the same level.
Previously, phishing actors would impersonate CEOs and CFOs to trick company employees in targeted phishing attacks.
This made sense because sending instructions and making urgent requests as a high-ranking employee increases the chances of compliance by the recipient of these messages.
However, as the CEOs got more vigilant and security teams in large firms added more safeguards around those “critical” accounts, phishing actors turned to lower ranking employees that can still serve as excellent entry points into corporate networks.
"Security admins might be spending a lot of time providing extra attention to the C-Suite and hackers have adjusted. At the same time, non-executives still hold sensitive information and have access to financial data. Hackers realized, there is no need to go all the way up the food chain." - Avanan
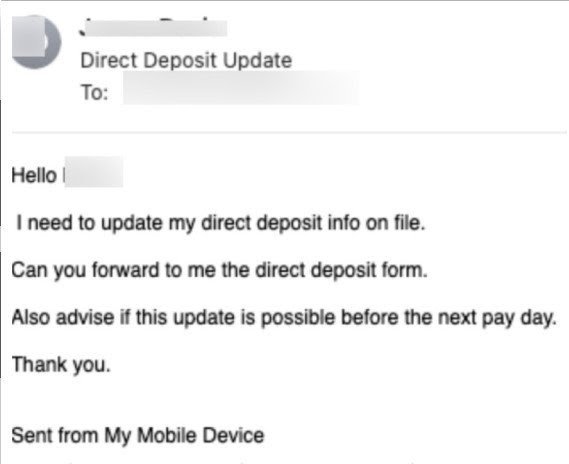
An example of this practice is given below, where an employee who has access to internal financial systems receives an urgent request to update the impersonated sender's direct deposit file info.
Phishing passwords with DocuSign
As Avanan details in its report, a typical trick deployed in these campaigns is the involvement of DocuSign, an otherwise legit cloud-based document signing platform.
The actors offer DocuSign as an alternate signing method in the emails they send, and ask the recipients to enter their credentials to view the document and sign it.
While these emails are crafted to look like legitimate DocuSign messages, they are not being sent from the platform. On real DocuSign emails, users are never asked to enter passwords, but rather an authentication code is emailed to the recipient.
In the haste of daily work, it is likely that some employees will be tricked by this message and treat it as a real DocuSign request, entering their email credentials and handing them over to the phishing actors
When an email lands in your inbox, it is crucial to take the time and evaluate it for any signs of trickery. Unsolicited attachments, spelling errors, and the request to enter your credentials should be treated as big red flags.
Docusign-themed phishing attacks are nothing new and have been used by numerous threat actors to steal login credentials and distribute malware. In August 2019, a campaign using DocuSign landing pages took it a step further by trying to trick people into entering their full credentials for a wide selection of email providers.
Source: bleepingcomputer
from TechCrunch https://ift.tt/3viO1C6
via IFTTT

Comments
Post a Comment