Just one-third of the 2020 U.S. presidential candidates are using an email security feature that could prevent a similar attack that hobbled the Democrats’ during the 2016 election.
Out of the 21 presidential candidates in the race according to Reuters, seven Democrats and one Republican candidate are using and enforcing DMARC, an email security protocol that verifies the authenticity of a sender’s email and rejects spoofed emails, which hackers often use to try to trick victims into opening malicious links from seemingly known individuals.
It’s a marked increase from April, where only Elizabeth Warren’s campaign had employed the technology. Now, the Democratic campaigns of Joe Biden, Kamala Harris, Michael Bloomberg, Amy Klobuchar, Cory Booker, Tulsi Gabbard, and Republican candidate Steve Bullock have all improved their email security.
The remaining candidates, including presidential incumbent Donald Trump, are not rejecting spoofed emails. Another seven candidates are not using DMARC at all.
That, experts say, puts their campaigns at risk from foreign influence campaigns and cyberattacks.
“When a campaign doesn’t have the basics in place, they are leaving their front door unlocked,” said Armen Najarian, chief identity officer at Agari, an email security company. “Campaigns have to have both email authentication set at an enforcement policy of reject and advanced email security in place to be protected against socially-engineered covert attacks,” he said.
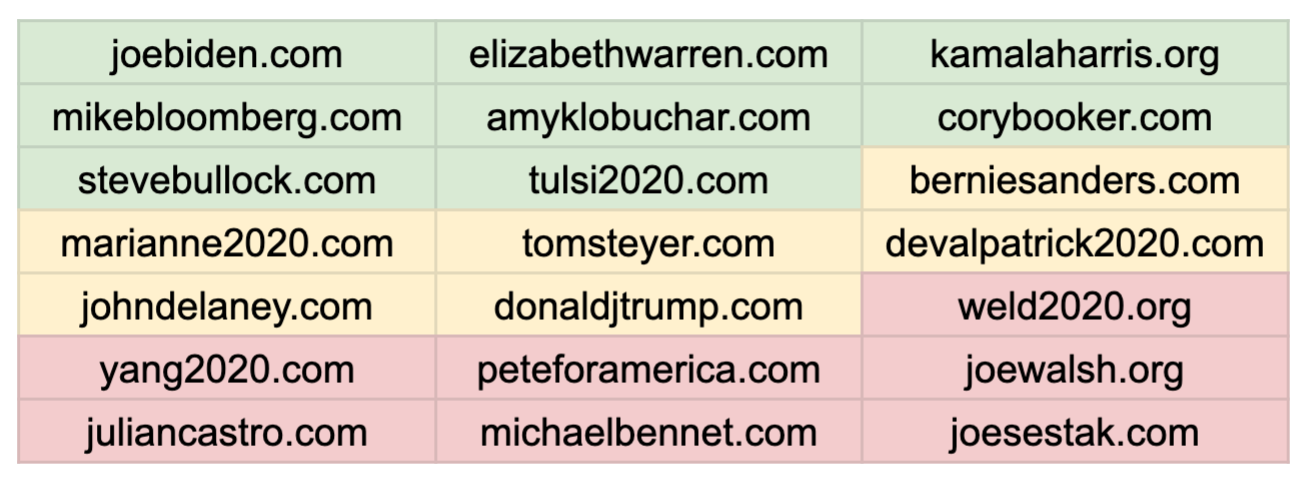
Green indicates a reject/quarantine policy, while yellow indicates a non-enforced policy. (Image: TechCrunch)
DMARC, which is free and fairly easy to implement, can prevent attackers from impersonating a candidate’s campaign but also prevent the same kind of targeted phishing attacks against the candidate’s network that resulted in the breach and theft of thousands of emails from the Democrats.
In the run-up to the 2016 presidential election, Russian hackers sent an email to Hillary Clinton campaign manager John Podesta, posing as a Google security warning. The phishing email, which was published by WikiLeaks along the rest of the email cache, tricked Podesta into clicking a link that took over his account, allowing hackers to steal tens of thousands of private emails.
A properly enforced DMARC policy would have rejected the phishing email from Podesta’s inbox altogether, though DMARC does not protect against every kind of highly sophisticated cyberattack. The breach was bruising for the Democrats, one that led to high-profile resignations and harmed public perceptions of the Clinton presidential campaign — one she ultimately lost.
“It’s perplexing that the campaigns are not aggressively jumping on this issue,” said Najarian.
from TechCrunch https://ift.tt/2rtgisG
via IFTTT
Comments
Post a Comment